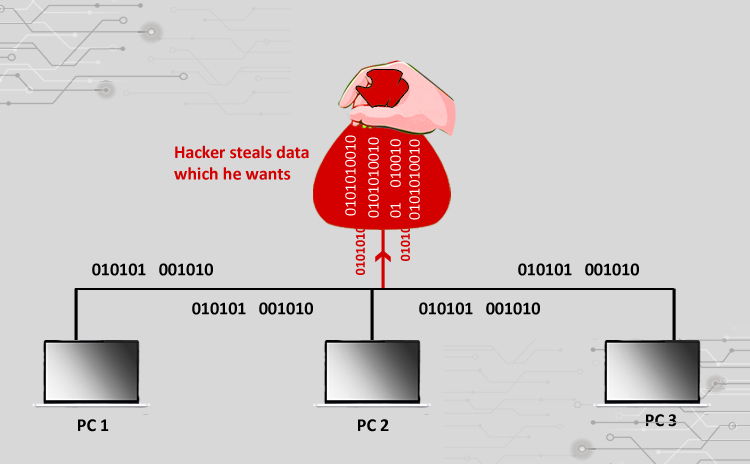
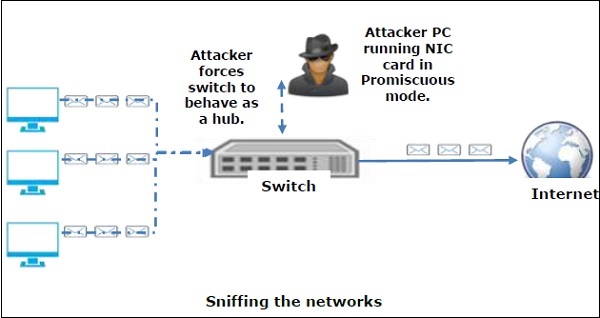
TechForing Ltd. on Twitter: "IoT Sniffer Attack. Sniffers intercepts your data like passwords, image and other important private data. #iotsniffing #sniffingattack #cyberattack #cybersecurity #techforingcybersecurity https://t.co/WgPHE6F89p" / Twitter

Network Packet Sniffer on Various Network Protocols on Live Network | by vaibhav sharma | Vaibhav Sharma | Medium