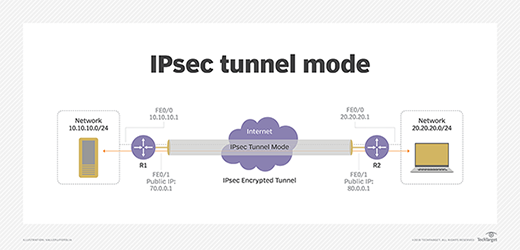
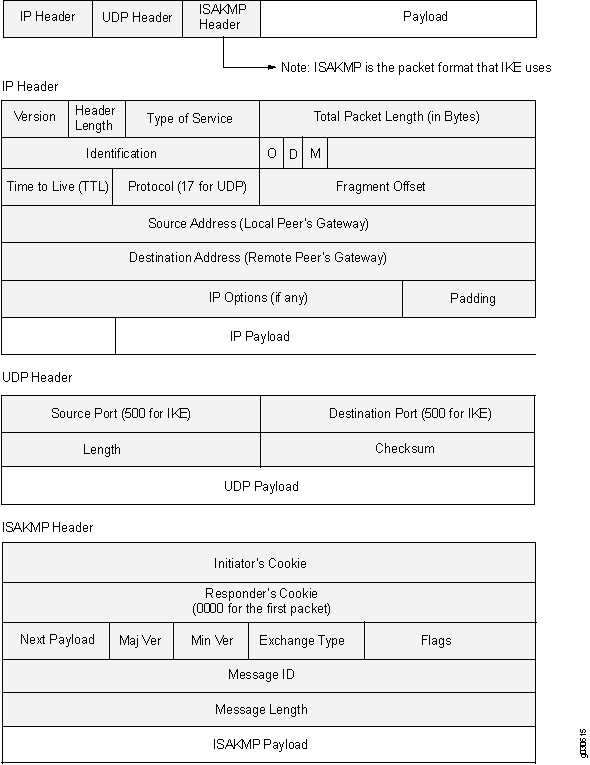
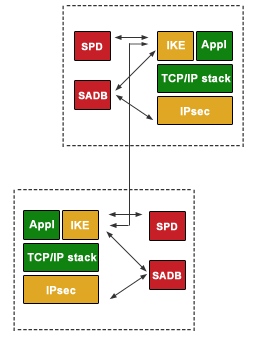
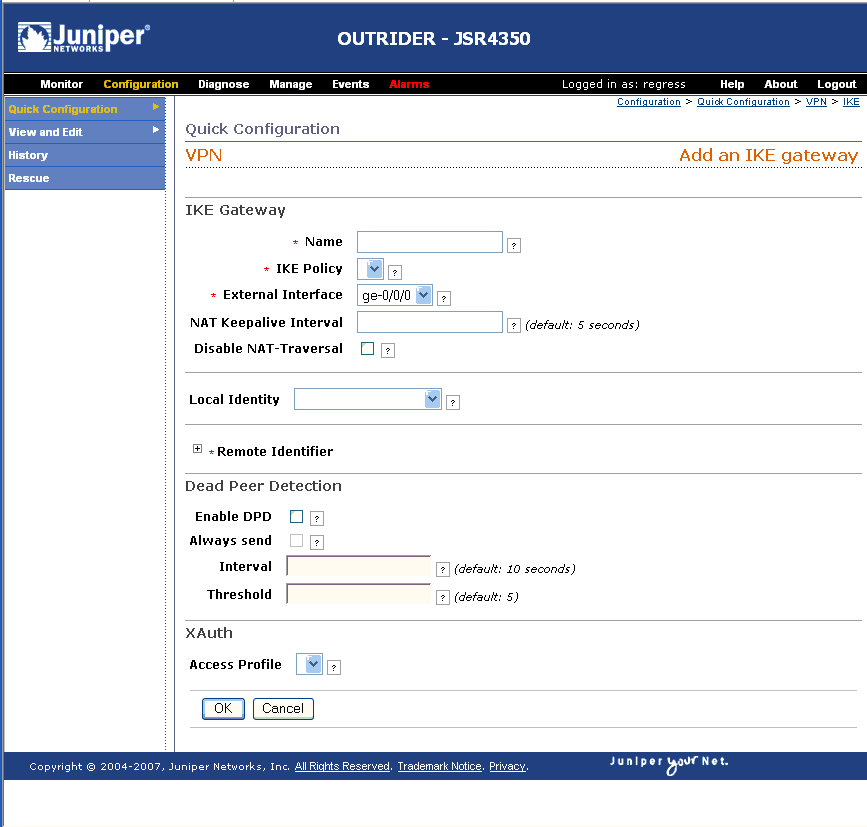
Using an ACL to Establish an IPSec Tunnel - AR500, AR510, and AR530 V200R007 CLI-based Configuration Guide - VPN - Huawei

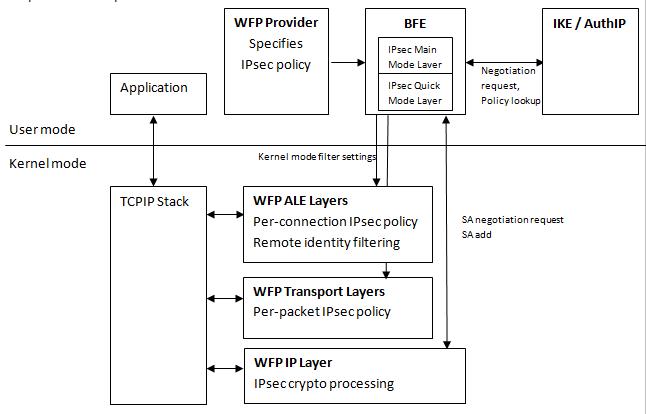
ECC Based IKE Protocol Design for Internet Applications – topic of research paper in Computer and information sciences. Download scholarly article PDF and read for free on CyberLeninka open science hub.